

We celebrate all kinds of manufacturing at AMT – The Association For Manufacturing Technology, from the most cutting-edge smart automation to the humble, time-honored shuttle loom. Few things thread the needle between tradition and tech quite like denim.


Check in for the highlights, headlines, and hijinks that matter to manufacturing. These lean news items keep you updated on the latest developments.


New technology is a growth engine for manufacturing, but change risks disruption and enormous costs. Incrementally rolling out new equipment and software using technology testbeds helps refine and optimize processes before production deployment.


Check in for the highlights, headlines, and hijinks that matter to manufacturing. These lean news items keep you updated on the latest developments.


Successfully implementing edge computing into your shop floor may be more cost efficient than you think! Here are a couple ways your shop (and budget) can benefit. Bonus: Edge computing devices can also bolster your cybersecurity measures, saving you more!


In collecting data for digital manufacturing, the underlying system architecture for collecting and storing the data can significantly impact the system's benefits and its flexibility for future extensions. We examine two types that may address your needs.


Event to Connect Small and Medium Manufacturers with Experts in Smart Technologies
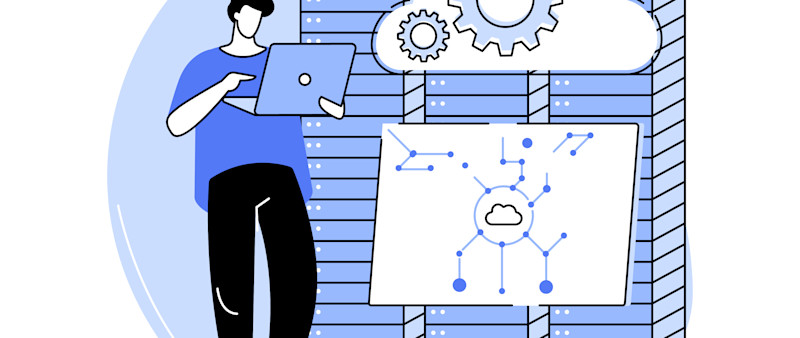
Edge computing in digital manufacturing involves placing devices between data sources and the network, and ranges from basic data collection to distributed systems. Learn more about its benefits like data processing, isolation, organization, and security.


What are the benefits of harvesting semantic data from equipment on the shop floor? For starters, it's easier to integrate machines into shop maintenance and monitoring systems. Learn how the industry has responded to semantic data – and where it's going.
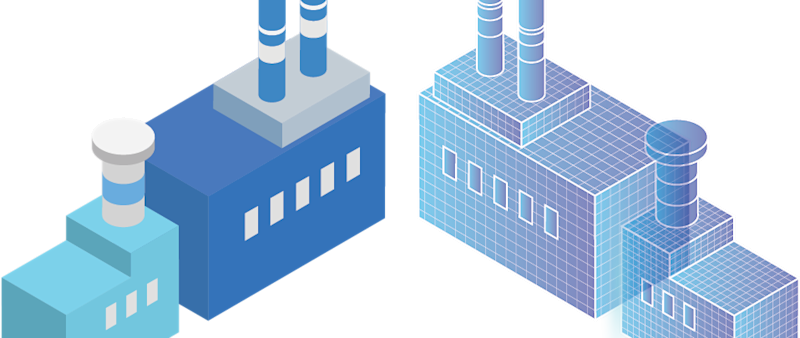
A digital twin is more than a computer approximation or simple 3D model – it is an ever-evolving, data-driven digital representation of a system.
