Your biggest cybersecurity threat is you. You and all your fellow humans. To protect your company from cybercrime, you have to focus on reducing human error. There is a lot of room for improvement.
According to Verizon’s Data Breach Investigations Report, a staggering 74% of cybersecurity breaches are driven by the human element. Criminals are cashing in on the vulnerabilities caused by the human element through a process known as social engineering.
Understanding Social Engineering
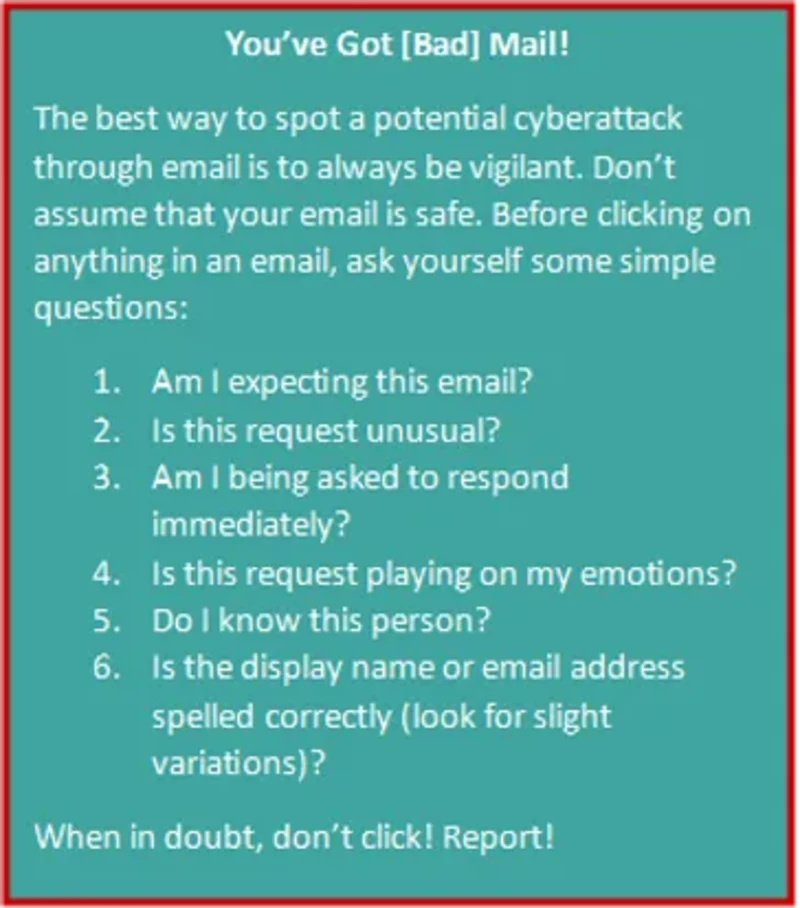
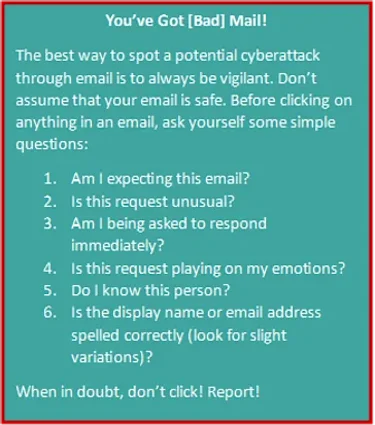
Social engineering is the act of manipulating people into doing something they may not want to do. Cybercriminals work to get users to divulge confidential information that can be used to commit various crimes — from information mining to complete system takeovers for ransom. The vast majority of social engineering attacks begin with email phishing.
Phishing isn’t new. We’ve all been offered a fortune from a long-lost foreign relative who just needed our bank account number. Unfortunately, phishing has gotten more customized and complex over the years. Often, attacks now come from a “friendly source” — which might include an email address you think you recognize or a company name that looks familiar (sometimes with a slight misspelling). And, as always, the attacks play on human emotion to get people to act without thinking.
Artificial intelligence is also being deployed to make phishing emails more real and sophisticated. Tools like ChatGPT help criminals ensure that their emails use proper English and sound convincing.
In the face of increasingly sophisticated, nebulous criminals, what can you do? A lot. Start here.
1. Prioritize real threats.
You don’t need to create dramatic scenarios or once-in-a-lifetime breaches. Real security threats are happening every day — likely to you. Most security threats come in through email. If you’ve got email, you’re a potential risk. Make sure you are using multifactor identification for email. Utilize the security tools that are built into G-suite and Office 360. Use antivirus software and keep systems updated.
2. Focus on awareness.
No matter how much you prioritize, there will still be cyber threats, and some will get through. Now, you need to minimize risk by focusing on awareness. User education is key. Teach users to spot phishing threats — and report them. Phishing simulation tests are a great way to prepare employees. People still fall for scams that make them feel fearful or curious. Make sure staff at every level know that email is not innocuous.
3. Train, train, train.
Cybercrime is now offered as a service — meaning that professional hackers and scammers are working full time to bait, switch, and trick. Small to medium manufacturers in particular have to prioritize cybersecurity training because a single attack could damage or even eliminate their business.
Employees need to receive regular training. Security awareness training providers make the cybersecurity training process more dynamic and engaging — making it more likely to work. Even after training, you will likely have some outliers who will click on bad links but bringing that number way down will go a long way toward protecting your business.
4. Build (and encourage) good cyber habits.
Most people already have bad cyber hygiene. They don’t use strong passwords. They don’t use password managers. They click ALL the links or open the attachments in their emails. They don’t report suspicious emails. Now it is time to build good cyber habits.
Teach employees the why and how for cybersecurity. Educate them on building stronger passwords and using password managers. Show them what a healthy skepticism of email looks like. Help them to understand why reusing the same password all the time will lead to a quick data breach. Building a habit takes time and practice. Start to foster a security culture through strong leadership, training, and frequent reminders.
With time and practice, it is possible to clean up your cyber act and stop cybercrime — from the inside.




